NEWNow you’ll be able to take heed to Fox Information articles!
Phishing scams goal all forms of establishments, be it a hospital, a big expertise firm or perhaps a quick meals chain. Academic establishments aren’t any exception, particularly in 2025 when attackers are actively focusing on them. US universities face a brand new kind of cybercrime the place attackers goal staff to hijack wage funds. Researchers found that since March 2025, a bunch of hackers often called Storm-2657 has been finishing up “pirate payroll” assaults, utilizing phishing techniques to achieve entry to payroll accounts. Let’s speak extra about this assault and how one can keep protected.
Join my FREE CyberGuy report
Obtain my greatest tech ideas, pressing safety alerts, and unique provides straight to your inbox. Plus, you may get instantaneous entry to my Final Rip-off Survival Information – without cost whenever you be a part of my CYBERGUY.COM. publication.
Scammers now pose as co-workers and steal e-mail threads in convincing phishing assaults
How the College Payroll Rip-off Works
In accordance with Microsoft Menace Intelligence, Storm-2657 is primarily focusing on Workday, a broadly used human assets platform, though different payroll and HR software program may be in danger. Attackers begin with extremely convincing phishing emails, rigorously crafted to draw particular person crew members. Some messages warn of a sudden outbreak of sickness on campus, creating a way of urgency, whereas others state {that a} school member is beneath investigation, urging recipients to verify paperwork instantly. In some instances, the emails impersonate the college president or HR division, sharing “necessary” updates about compensation and advantages.

Phishing scams are evolving quickly and now universities have change into prime targets for payroll theft. (Kurt “CyberGuy” Knutsson)
These emails include hyperlinks designed to seize login credentials and multi-factor authentication (MFA) codes in actual time utilizing man-in-the-middle adversary methods. As soon as a workers member enters their info, attackers can entry the account as in the event that they have been the reliable person. As soon as they acquire management, hackers arrange inbox guidelines to delete Workday notifications so victims do not see alerts about adjustments. This stealthy method permits attackers to switch payroll profiles, regulate wage cost settings, and redirect funds to accounts they management, all with out elevating fast suspicion.
COLUMBIA UNIVERSITY DATA BREACH AFFECTS 870,000 PEOPLE
Hackers are exploiting universities on a big scale
Hackers do not cease at a single account. As soon as they management a mailbox, they use it to additional unfold the assault. Microsoft studies that from simply 11 compromised accounts at three universities, Storm-2657 despatched phishing emails to almost 6,000 e-mail addresses at 25 establishments. Through the use of trusted inner accounts, your emails seem extra reliable, making recipients extra more likely to fall for the rip-off.
To keep up entry over time, attackers generally enroll their very own cellphone numbers as MFA units, by Workday or Duo MFA profiles. This provides them persistent entry, permitting them to enact additional malicious actions with out having to phish once more. Mixed with inbox guidelines that conceal notifications, this technique permits them to function undetected for longer intervals of time.
Microsoft emphasizes that these assaults don’t exploit a flaw in Workday itself. As a substitute, they depend on social engineering, the absence of robust, phishing-resistant MFA, and cautious manipulation of inner programs. In essence, the risk comes from human conduct and inadequate safety, not software program bugs.
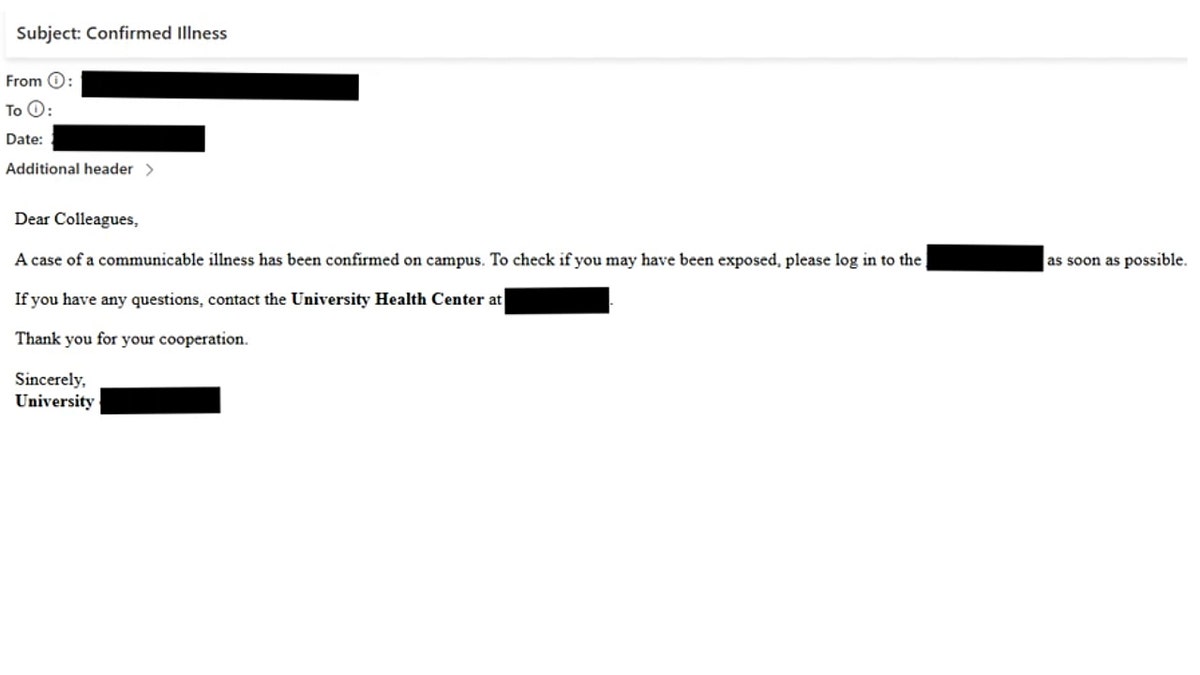
Hackers lure workers with convincing emails that mimic campus alerts or HR updates and steal real-time login particulars. (Microsoft)
6 Methods to Shield Your self Towards Payroll and Phishing Scams
Defending your self towards payroll and phishing scams is not sophisticated. By taking just a few cautious steps, you may make it a lot more durable for attackers to achieve entry to your accounts or private info.
1) Restrict what private info is on-line
The extra info scammers discover about you, the better it is going to be to create convincing phishing messages. Companies that take away or monitor private information on-line can scale back publicity by making it more durable for attackers to trick you with focused emails.
Though no service can assure full elimination of your information from the Web, an information elimination service is certainly a wise alternative. They don’t seem to be low-cost and neither is your privateness. These companies do all of the be just right for you, actively monitoring and systematically deleting your private info from tons of of internet sites. It is what provides me peace of thoughts and has confirmed to be the simplest solution to delete your private information from the web. By limiting the knowledge obtainable, you scale back the chance of scammers cross-referencing breach information with info they could discover on the darkish internet, making it more durable for them to focus on you.
Try my high picks for information elimination companies and get a free verify to seek out out in case your private info is already on the internet by visiting Cyberguy. with.
Run a free verify to seek out out in case your private info is already on the internet: Cyberguy.com
2) Suppose earlier than you click on
Scammers typically ship emails that seem to return from the HR division or college management, alerting you about payroll, advantages, or pressing points. Don’t click on on hyperlinks or obtain attachments until you’re 100% positive they’re reliable. Even small errors may give attackers entry to your accounts.
One of the simplest ways to guard your self from malicious hyperlinks is to have antivirus software program put in on all of your units. This safety may also warn you to phishing emails and ransomware scams, conserving your private info and digital property protected.
Get my picks for 2025’s greatest antivirus safety winners in your Home windows, Mac, Android, and iOS units at Cyberguy. with.

Researchers found that since March 2025, a bunch of hackers often called Storm-2657 has been finishing up “pirate payroll” assaults, utilizing phishing techniques to achieve entry to payroll accounts. (Javi Sanz/Getty Pictures)
3) Examine immediately with the supply
If an e-mail mentions wage adjustments or requires motion, name or e-mail the HR workplace or the particular person immediately, utilizing the contact info you already know. Phishing emails are designed to create panic and hasty choices, so taking a second to verify can deter attackers.
4) Use robust and distinctive passwords
By no means reuse passwords throughout a number of accounts. Scammers typically attempt to use credentials stolen from different breaches. A password supervisor might help you generate robust passwords and retailer them securely so you do not have to recollect dozens of various mixtures.
Subsequent, see in case your e-mail has been uncovered in earlier breaches. Our #1 password supervisor decide features a built-in breach scanner that checks whether or not your e-mail tackle or passwords have appeared in identified breaches. Should you uncover a match, instantly change any reused passwords and safe these accounts with new, distinctive credentials.
Try the very best expert-reviewed password managers of 2025 at Cyberguy. with.
5) Allow two-factor authentication (2FA)
Add an additional layer of safety by enabling 2FA on all accounts that assist it. Because of this even when somebody steals your password, they nonetheless will not have the ability to log in with no second verification step, like a code despatched to your cellphone.
6) Frequently verify monetary and payroll accounts
Even should you observe all precautions, it’s advisable to observe your accounts for any uncommon exercise. Shortly detecting unauthorized transactions can stop bigger losses and warn you to potential fraud earlier than it escalates.
CLICK HERE TO DOWNLOAD THE FOX NEWS APP
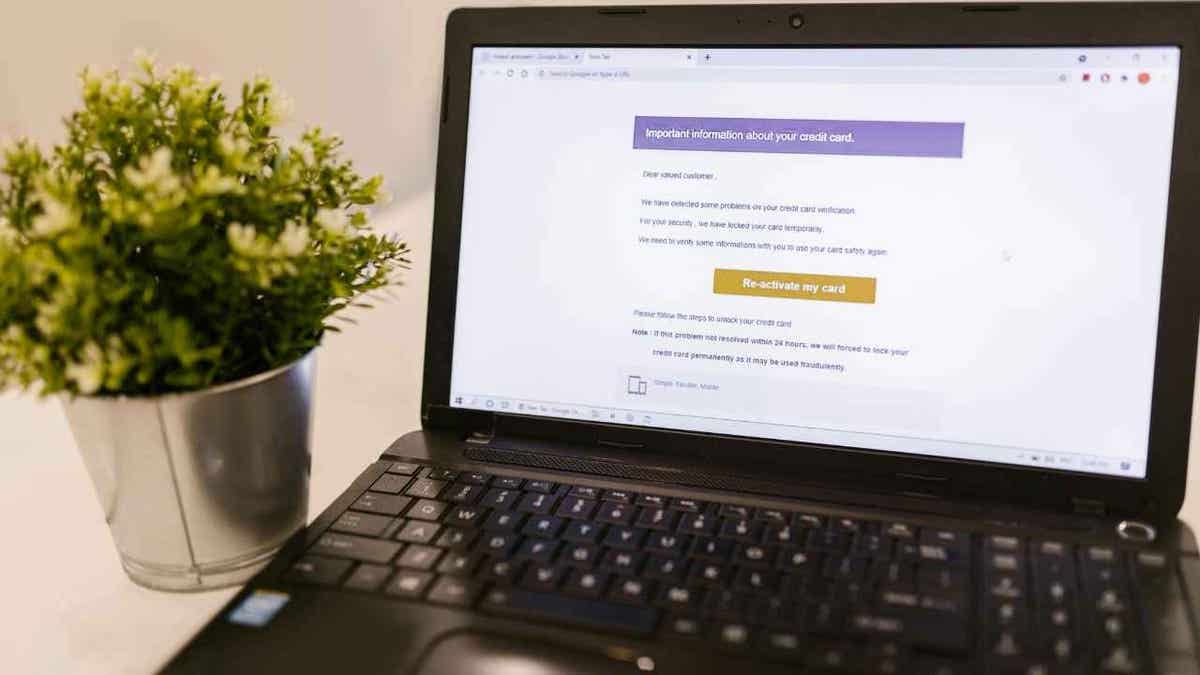
Hackers will redirect funds after getting access to customers’ login info. (Kurt “CyberGuy” Knutsson)
Kurt’s foremost lesson
The Storm-2657 assaults present that cybercriminals are focusing on belief, not software program. Universities are engaging as a result of payroll programs deal with cash immediately and staff will be manipulated by well-crafted phishing. The dimensions and class of those assaults highlights how susceptible even well-established establishments will be to financially motivated risk actors.
How typically do you verify your payroll or financial institution accounts for uncommon exercise? Tell us by writing to us at Cyberguy. with.
Join my FREE CyberGuy report
Obtain my greatest tech ideas, pressing safety alerts, and unique provides straight to your inbox. Plus, you may get instantaneous entry to my Final Rip-off Survival Information – without cost whenever you be a part of my CYBERGUY.COM. publication.
Copyright 2025 CyberGuy.com. All rights reserved.

Leave a Reply